Sveiki papasakosim apie crypto virusus arba ransomware arba sifruojantis virusas. Sis virusas turi ivariu pavadinimu atmainu bet galutinis rezultatas tas pats uzkoduoti failai ir ispirka.
Visa viruso eiga
1. Jus i pasta gaunat laiska. dazniausiai laiskas yra doc su pavadinimu invoice arba saskaita arba kolego laiskas su vardu kazkuriuo. ir dazniausiai buna prirasyta jus gavote saskaita prasome greiciau perziureti ir apmoketi.
kaip zmogus paspaudzia atidaryti jam gali dar ismesti lentele enable macros. ir kaip tik zmogus paspaudzia virusas isipakuoja ir pradeda veikti.
pradeda ieskotu failu
|
Office/Document files (62x): dokumentai |
.123, .602, .CSV, .dif, .DOC, .docb, .docm, .docx, .DOT, .dotm, .dotx, .hwp, .mml, .odg, .odp, .ods, .odt, .otg, .otp, .ots, .ott, .pdf, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .PPT, .pptm, .pptx, .RTF, .sldm, .sldx, .slk, .stc, .std, .sti, .stw, .sxc, .sxd, .sxi, .sxm, .sxw, .txt, .uop, .uot, .wb2, .wk1, .wks, .xlc, .xlm, .XLS, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml |
|
Scripts/Source codes (23x): |
.asm, .asp, .bat, .brd, .c, .class, .cmd, .cpp, .cs, .dch, .dip, .h, .jar, .java, .js, .pas, .php, .pl, .rb, .sch, .sh, .vb, .vbs |
|
Media files (20x): |
.3g2, .3gp, .asf, .avi, .fla, .flv, .m3u, .m4u, .mid, .mkv, .mov, .mp3, .mp4, .mpeg, .mpg, .swf, .vob, .wav, .wma, .wmv |
|
Graphic/Image files (14x): nuotraukos |
.bmp, .cgm, .djv, .djvu, .gif, .jpeg, .jpg, .NEF, .png, .psd, .raw, .svg, .tif, .tiff |
|
Database files (14x): |
.db, .dbf, .frm, .ibd, .ldf, .mdb, .mdf, .MYD, .MYI, .odb, .onenotec2, .sql, .SQLITE3, .SQLITEDB rivile centas finvalda agnumas |
|
Archives (11x): |
.7z, .ARC, .bak, .gz, .PAQ, .rar, .tar, .bz2, .tbk, .tgz, .zip |
|
CAD/CAM/3D files (8x): |
.3dm, .3ds, .asc, .lay, .lay6, .max, .ms11, .ms11 (Security copy) |
|
Certificates (5x): |
.crt, .csr, .key, .p12, .pem |
|
Virtual HDD (4x): |
.qcow2, .vdi, .vmdk, .vmx |
|
pastas (2x): |
pst outlook windows mail |
|
Virtual currency (1x): |
wallet.dat bitcoin litecoin pinigines |
Surades situos failus virusus iskart juos sifruoja. dazniausiai vadinimu AES sifrafimu.
https://lt.wikipedia.org/wiki/AES
raktas sugeneruojamas automatiskai kiek yra zinoma kad ta pacia diena dazniausiai toks pats.
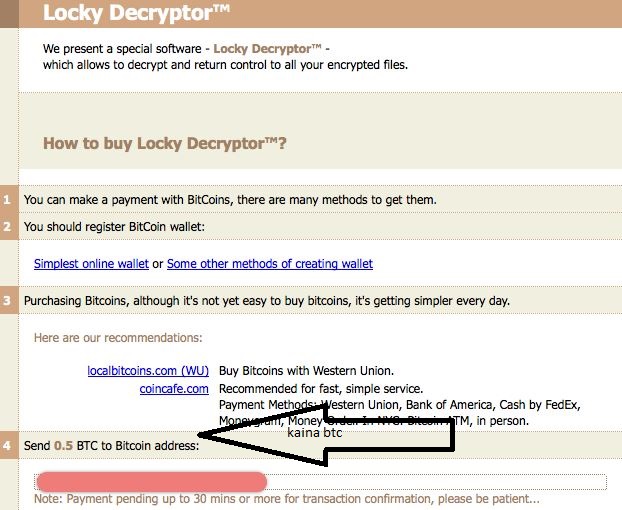
uzsifraves duomenis virusas pasisalina ir palieka instrukcija kaip atgauti failus su kaina. kaina nurodoma bitcoint tam kad negalima butu atrasti kuriam zmogui pervedet.
Musu labaratorija yra pastebejus kad siai dienai virusas dazniausiai paveikia kompiuterius kurie neturi antivirus bet yra pastebeta ir su antivirusais
antivirusines kurios buvo kompiuteri bet nesustabde virus
NOD 4 5 6 versija
Siuloma antivirusai kurie yra atparus virusam !!!
Kaspersky internet security atsisiusti cia nemokamai galioja 30 dienu
360 total security nemokama antivirusas atsiusti cia
Jeigu jau pasigavot tai antivirusas jau nepades jum atgauti duomenu.
Atgauti duomenis yra galimi keli variantai
1. kadangi virusas trina failus galima meginti atrasti kaip istrintus failus su atkurimo programa skirta istrinetiem duomenim
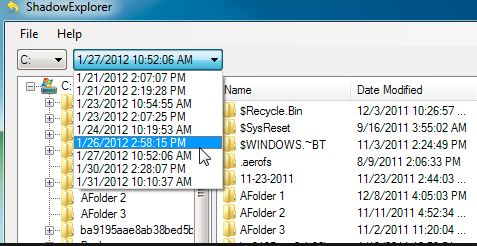
2. Jeigu virusas nespejo padaryti viso darbo pvz zmogus nutrauke viruso darba. galima meginti su programele
http://www.shadowexplorer.com/downloads.html .
bet siuloma yra pasidaryti disko kopija pradziai pries bet ka darant kad poto suklydus galima kazka dar pasidaryti
Posektorinė kopija 1:1
| Iki 1 TB | 30,00 Eur + PVM |
| Nuo 1 iki 2 TB | 50,00 Eur + PVM |
| Nuo 2 iki 3 TB | 70,00 Eur + PVM |
| Nuo 3 TB ir daugiau | nuo 90,00 Eur + PVM |
3 variantas sumoketi ispirka. esama tokiu variantu kaip zmonem reikejo duomenu teko ir moketi. is patirties sumokejus gaunama 100% raktas atkuodoti failus bet ne visada 100% atsifruoja. ir duomenu atstatyti neimanoma visai
4 variantas jai nezinot ka daryti ar nenorit daryti pristatyti i artimiausiai musu skyriu ir musu profesionalus techinkai bandys jum padeti
Virusai ( Duomenu atstatymo kainos )
| Paprasti virusai | 20 - 50 Eur + PVM |
| CryptoLocker | nuo 50 Eur + PVM |
| CryptoWall | nuo 70 Eur + PVM |
| Kiti virusai gadintais duomenys | nuo 100 Eur +pvm |
Yra jau irankiu kurie leidzia atsifruoti duomenis nemokat pinigu siai dienai mes turim sitiem virusam sprendimus sukurtus musu labaratorijoje
777
Apocalypse
Locky
Badblock
Crypboss
Cryptinfinite
Dryptodefense
Dmalocker2
Gomasom
Harasom
Hydra
Keybtc
Lechiffre
Nemucod
Pclok
Radamant
Stampado
Tesla 1 2 3
Wildfire
Xor
Shade
Rakhni
Mp3
Bart
Crypt888
Legion
| CryptXXX V1, V2, V3* | {original file name}.crypt, cryp1, crypz, or 5 hexadecimal characters |
| CryptXXX V4, V5 | {MD5 Hash}.5 hexadecimal characters |
| TeslaCrypt V1** | {original file name}.ECC |
| TeslaCrypt V2** | {original file name}.VVV, CCC, ZZZ, AAA, ABC, XYZ |
| TeslaCrypt V3 | {original file name}.XXX or TTT or MP3 or MICRO |
| TeslaCrypt V4 | File name and extension are unchanged |
| SNSLocker | {Original file name}.RSNSLocked |
| AutoLocky | {Original file name}.locky |
| BadBlock | {Original file name} |
| 777 | {Original file name}.777 |
| XORIST | {Original file name}.xorist or random extension |
| XORBAT | {Original file name}.crypted |
| CERBER V1 | {10 random characters}.cerber |
| Stampado | {Original file name}.locked |
| Nemucod | {Original file name}.crypted |
| Chimera | {Original file name}.crypt |
| LECHIFFRE | {Original file name}.LeChiffre |
| MirCop | Lock.{Original file name} |
| Bart | {Original file name}.bart.zip |
| Apocalypse | {Original file name}.encrypted, .FuckYourData, .locked, .Encryptedfile, or .SecureCrypted |
| Crypt888 | Lock.{Original file name} |
| Legion | {Original file name}_23-07-2016-21-27-23_$ |
| Jigsaw | {Original file name}.random extension |
| Globe/Purge |
V1: {Original file name}.purge V2: {Original file name}.{email address + random characters} V3: Extension not fixed or file name encrypted |
| DXXD |
V1: {Original file name}.{Original extension}dxxd |
| Teamxrat/Xpan |
V2: {Original filename}.__xratteamLucked |
| Crysis | |
| DemoTool |
.demoadc |
| PowerLocky |
{Original file name}.locky |
| TeleCrypt |
{Original file name} |
| DemoTool | .demoadc |
| Dharma | .wallet |
| WannaCry (WCRY) | {Original file name}.WNCRY, {Original file name}.WCRY |
| AES_NI | |
| XData | {Original file name} XData |
| Jaff | {Original file name} WLU |
| NemucodAES | |
| LambdaLocker | .lambda_l0cked |
| Petya |
Siuo metu ieskome budu ir neturim sitiem virusam !!!
ZEPTO virusas Atsifruoti 5% duomenu siai dienai
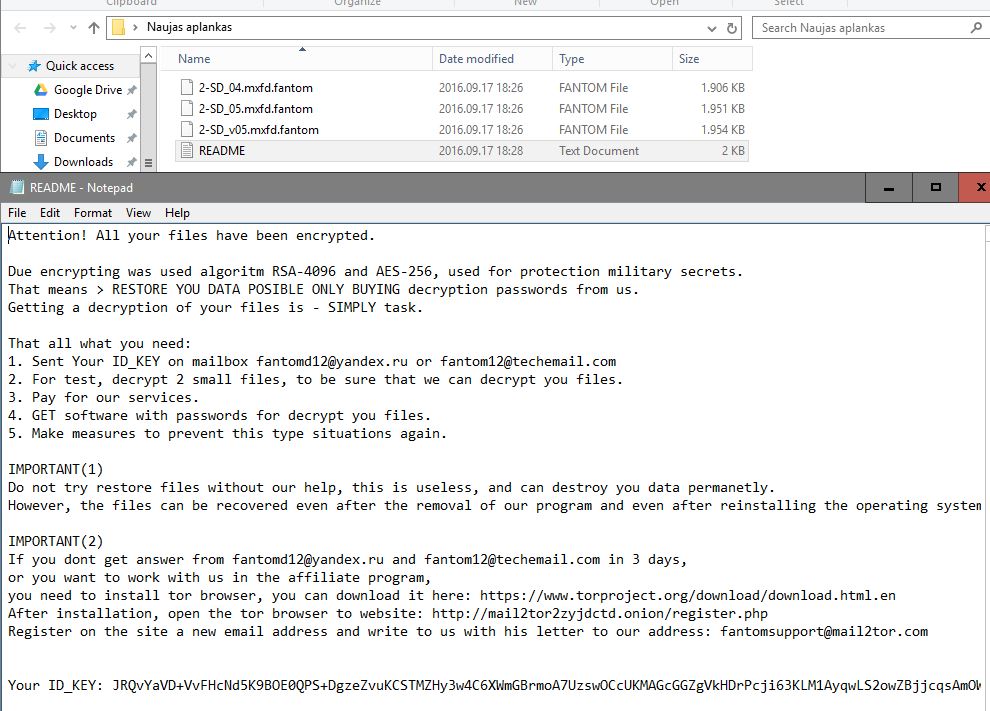
Fantom virusas Atsifruoti 1.8 %
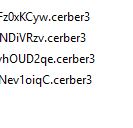
Cerber3 Virusas atsifruoti 0.7 %
cerber 4-5
Osiris
Jeigu duomenys nera skubus bet svarbus siuloma pasilikti kopija. Dazniausiai laboratorija atranda irankius kazkur 0.5- 1 metu begyje. !!!
Atnaujinta 2017-11-15
Visi imanomi
777, 7ev3n, 7h9r, 7zipper, 8lock8, ACCDFISA v2.0, AdamLocker, AES_KEY_GEN_ASSIST, AES-NI, Al-Namrood, Al-Namrood 2.0, Alcatraz, Alfa, Alma Locker, Alpha, AMBA, Amnesia, AnDROid, AngryDuck, Anubis, Apocalypse, Apocalypse (New Variant), ApocalypseVM, ASN1 Encoder, AutoLocky, AxCrypter, BadBlock, BadEncript, BandarChor, BankAccountSummary, Bart, Bart v2.0, BitCrypt, BitCrypt 2.0, BitCryptor, BitKangoroo, BitStak, Black Feather, Black Shades, Blocatto, BlockFile12, Booyah, BrainCrypt, Brazilian Ransomware, BTCamant, BTCWare, Bucbi, BuyUnlockCode, Cancer, Cerber, Cerber 2.0, Cerber 3.0, Cerber 4.0 / 5.0, CerberTear, Chimera, CHIP, Clouded, CockBlocker, Coin Locker, CoinVault, Comrade Circle, Conficker, Coverton, CradleCore, Cripton, Cry128, Cry9, Cryakl, CryFile, CryLocker, CrypMic, CrypMic, Crypren, Crypt0, Crypt0L0cker, Crypt38, CryptConsole, CryptFuck, CryptInfinite, CryptoDefense, CryptoDevil, CryptoFinancial, CryptoFortress, CryptoHasYou, CryptoHitman, CryptoJacky, CryptoJoker, CryptoLocker3, CryptoLockerEU, CryptoLuck, CryptoMix, CryptoMix Revenge, CryptoMix Wallet, CryptON, Crypton, CryptorBit, CryptoRoger, CryptoShield, CryptoShocker, CryptoTorLocker, CryptoViki, CryptoWall 2.0, CryptoWall 3.0, CryptoWall 4.0, CryptoWire, CryptXXX, CryptXXX 2.0, CryptXXX 3.0, CryptXXX 4.0, CryPy, CrySiS, CTB-Faker, CTB-Locker, Damage, DarkoderCryptor, Deadly, DEDCryptor, DeriaLock, Dharma (.dharma), Dharma (.onion), Dharma (.wallet), Digisom, DirtyDecrypt, DMA Locker, DMA Locker 3.0, DMA Locker 4.0, DMALocker Imposter, Domino, Done, DoNotChange, DXXD, DynA-Crypt, ECLR Ransomware, EdgeLocker, EduCrypt, El Polocker, EncrypTile, EncryptoJJS, Encryptor RaaS, Enigma, Enjey Crypter, EnkripsiPC, Erebus, Evil, Exotic, Extractor, Fabiansomware, Fadesoft, Fantom, FenixLocker, FindZip, FireCrypt, Flatcher3, FLKR, Flyper, FrozrLock, FS0ciety, FuckSociety, FunFact, GC47, GhostCrypt, Globe, Globe (Broken), Globe3, GlobeImposter, GlobeImposter 2.0, GOG, GoldenEye, Gomasom, GPCode, GX40, HadesLocker, HappyDayzz, Heimdall, Help50, HelpDCFile, Herbst, Hermes, Hermes 2.0, Hi Buddy!, HiddenTear, HollyCrypt, HolyCrypt, Hucky, HydraCrypt, IFN643, iRansom, Ishtar, Jack.Pot, Jaff, Jager, JapanLocker, JeepersCrypt, Jigsaw, Jigsaw (Updated), JobCrypter, JuicyLemon, Kaenlupuf, Karma, Karmen, Kasiski, KawaiiLocker, KeRanger, KeyBTC, KEYHolder, KillerLocker, KimcilWare, Kirk, Kolobo, Kostya, Kozy.Jozy, Kraken, KratosCrypt, Krider, Kriptovor, KryptoLocker, L33TAF Locker, LambdaLocker, LeChiffre, LLTP, LMAOxUS, Lock2017, Lock93, Locked-In, LockLock, Locky, Lortok, LoveServer, LowLevel04, MafiaWare, Magic, Maktub Locker, Marlboro, MarsJoke, Matrix, Maykolin, Meteoritan, Mikoyan, MirCop, MireWare, Mischa, MNS CryptoLocker, Mobef, MOTD, MRCR1, n1n1n1, NanoLocker, NCrypt, NegozI, Nemucod, Nemucod-7z, Netix, NewHT, Nhtnwcuf, NM4, NMoreira, NMoreira 2.0, NotAHero, Nuke, NullByte, NxRansomware, ODCODC, OpenToYou, OzozaLocker, PadCrypt, PayDay, PaySafeGen, PClock, PClock (Updated), PEC 2017, Philadelphia, Pickles, PopCornTime, Potato, PowerLocky, PowerShell Locker, PowerWare, Pr0tector, PrincessLocker, PrincessLocker 2.0, Project34, Protected Ransomware, PshCrypt, PyL33T, R980, RAA-SEP, Radamant, Radamant v2.1, RanRan, Rans0mLocked, RansomCuck, RansomPlus, RarVault, Razy, REKTLocker, RemindMe, RenLocker, RensenWare, Roga, Rokku, RoshaLock, RotorCrypt, Roza, RSAUtil, Ruby, Russian EDA2, SADStory, Sage 2.0, Salsa, SamSam, Sanction, Sanctions, Satan, Satana, SerbRansom, Serpent, ShellLocker, Shigo, ShinoLocker, Shujin, Simple_Encoder, Smrss32, SNSLocker, Spora, Sport, SQ_, Stampado, Stupid Ransomware, SuperCrypt, Surprise, SZFLocker, Team XRat, Telecrypt, TeslaCrypt 0.x, TeslaCrypt 2.x, TeslaCrypt 3.0, TeslaCrypt 4.0, TowerWeb, ToxCrypt, Trojan.Encoder.6491, Troldesh / Shade, TrueCrypter, TrumpLocker, UCCU, UIWIX, Ukash, UmbreCrypt, UnblockUPC, Ungluk, Unknown Crypted, Unknown Lock, Unknown XTBL, Unlock26, Unlock92, Unlock92 2.0, UserFilesLocker, USR0, Uyari, V8Locker, VaultCrypt, vCrypt, VenisRansomware, VenusLocker, VindowsLocker, Vortex, VxLock, WannaCryptor, WildFire Locker, Winnix Cryptor, WinRarer, WonderCrypter, X Locker 5.0, XCrypt, Xorist, Xort, XRTN, XTP Locker 5.0, XYZWare, YouAreFucked, YourRansom, zCrypt, Zekwacrypt, ZeroCrypt, ZimbraCryptor, ZinoCrypt, ZipLocker, Zyklon, Wanna Cry, AES-NI, XData, NemucodAES, LambdaLocker, Petya